Standalone installation¶
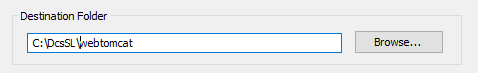
All components are installed under C:\DcsSL. This path can be freely selected, as addresses are always relative.
Installing the components¶
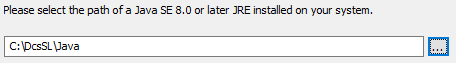
Installing Java 1.8.0_202¶
The JDK is installed under C:\DcsSL\Java. If we install the JRE instead, the directory must also be called Java so that the scripts can find Java (note the jsl configuration!).
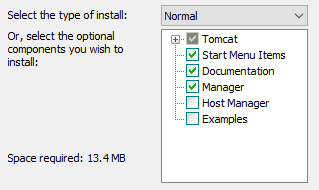
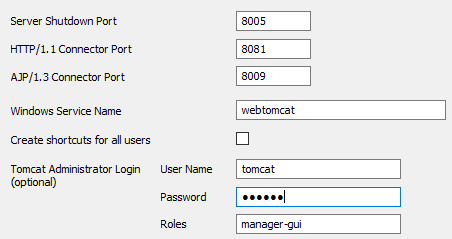
Installation of Tomcat 9.0.22¶
Installation to C:\DcsSL\webtomcat, service: webtomcat:
Installation of OneClickExt, ScriptLauncher, and WebSwing¶
Both components are delivered as tar archives: OneClickExtSa_d_2.5.10.tar.gz and OneClickExtSa_sl_2.5.10.tar.gz. WebSwing is in zip format.
- Unpack the archive
OneClickExtSa_d_2.5.10.tar.gztoC:\DcsSL\DICOS. - Unpack the archive
OneClickExtSa_sl_2.5.10.tar.gztoC:\DcsSL\webtomcat\webapps. - Unzip the archive
webswing-2.6.4.ziptoC:\DcsSL\webtomcat\webswing. - Copy the file
C:\DcsSL\webtomcat\webswing\webswing-server.wartoC:\DcsSL\webtomcat\webapps.
When upgrading, back up the existing files beforehand.
Configuration¶
ws_prepare_files script¶
The script C:\DcsSL\DICOS\OneClickExt\install\ws_prepare_files.bat is provided for configuration. After entering a few parameters, this script creates the files
jsl64.ini and webswing.config. The created files only need to be copied to the
correct location.
Example:
C:\DcsSL\DICOS\OneClickExt\install>ws_prepare_files.bat
Enter required parameters:
RMI Port: 16016
Base-URL (http://host:port):http://win10dev-ww 2 :
Base directory is C:/DcsSL
JSL workpath is C:\DcsSL\DICOS\OneClickExt\bin
JSL jrepath is C:\DcsSL\Java\jre
RMI-Port is 16016
Base-URL is http://win10dev-ww 2 :
creating new webswing.config ...
Installation Standalone
webswing.config created.
creating new jsl64.ini ...
jsl64.ini created.
creating new scriptlauncher.bat ...
scriptlauncher.bat created.
Verify webswing.config file and insert/copy to
C:/DcsSL/webtomcat/webswing/webswing.config
Uninstall Service oneclickexd before copy new jsl64.ini
Verify jsl64.ini file and copy to C:/DcsSL/DICOS/OneClickExt/bin/jsl64.ini
Verify scriptlauncher.bat file and copy to
C:/DCsSL/DICOS/OneClickExt/bin/scriptlauncher.bat
Append/Verify following lines in
C:/DcsSL/webtomcat/conf/catalina.properties
If installing on onclick use spectrum.war instead if webswing-server.war
webswing.warLocation=C:/DcsSL/webtomcat/webapps/webswing-server.war
webswing.configFile=C:/DcsSL/webtomcat/webswing/webswing.config
webswing.tempDirBase=C:/DcsSL/webtomcat/webswing/tmp
ScriptLauncher Daemon¶
The following parameters must be adjusted in the configuration file bin/oneclickext.props:
oneclickext.mls.primary: <Main Location Server>
oneclickext.mls.backup: <Backup Location Server>
oneclickext.ss.host: <Main SpectroSERVER>
oneclickext.ss.user: <Spectrum User>
oneclickext.rmi.port: <RMI Port>
oneclickext.rmi.connport: <RMI Connection Port>
Configure as service¶
If the daemon is to be managed as a Windows service, the service must first be set up. The jsl64.ini file generated by the script must be copied to the bin directory and the service set up. When updating, the service must first be uninstalled as an administrator in the bin directory:
jsl64 -remove
The setup can then be performed:
jsl64 -install
The following parameters can be checked in jsl64.ini beforehand:
wrkdir=C:/DcsSL/DICOS/OneClickExt/bin
jrepath=C:/DcsSL/Java/jre
jvmtype=server
For jvmtype, you must check the name of the directory containing the jvm.dll file: server or client. This directory is located in the Java bin directory.
OneClickExt can then be started as a service:
net start oneclickextd
WebSwing 2.6 configuration.¶
- Adjust the file
C:\DcsSL\webtomcat\server.xmlas needed, e.g., set port or enable https. - The file
C:\DcsSL\webtomcat\conf\catalina.propertiesmust be supplemented with the following parameters (output by the install script):webswing.warLocation webswing.configFile webswing.tempDirBase ``` - Copy the generated file webswing.config to `C:\DcsSL\webtomcat\webswing\webswing.config`. ### Setting up users Users can be created via the GUI or via the file `webswing.config` (see also 2.1 Post-installation). ### Setting up authentication via LDAP WebSwing does not support LDAP authentication out of the box. To authenticate via LDAP anyway, it must be enabled in Tomcat. Since a user logged in to Tomcat is unfortunately not transmitted to WebSwing, this must be implemented via a *Custom Security Module*. The entire authentication process can then be achieved via configuration. #### LDAP configuration The roles admin and scriptlauncher are used to control access to the different pages. Users are then assigned to the groups: Standalone installation #### Tomcat configuration The configuration in Tomcat consists of two parts: - Setting up the LDAP realm - Setting up the *security constraint* for each web app #### Tomcat LDAP realm The realm is set up globally in the file `<tomcat>/conf/server.xml`. To do this, the existing configuration is commented out and replaced with a new one: ```xml <Realm className="org.apache.catalina.realm.JNDIRealm" connectionName="cn=spectrum,dc=da,dc=dicos,dc=de" connectionPassword="<password>" connectionURL=“ldap://<Server>:<Port>” userPattern="cn={0},ou=users,dc=da,dc=dicos,dc=de" roleBase="ou=groups,dc=da,dc=dicos,dc=de" roleName="cn" roleSearch="(member={0})" />
Tomcat Security Constraint¶
For each web app, the permitted roles must be defined for the desired pages. In our case, we have the following pages (web apps):
http://localhost:8080
http://localhost:8080/sl
http://localhost:8080/webswing-server
For http://localhost:8080, a redirect to http://localhost:8080/sl is set up. To do this, the file <tomcat>/webapps/ROOT/index.jsp is replaced by an index.jsp with the following content:
<% response.sendRedirect(“/sl”); %>
WebApp /sl¶
Access to /sl is restricted to the scriptlauncher and admin roles. To do this, the file <tomcat>/webapps/sl/WEB-INF/web.xml must be extended as follows:
<?xml version="1.0" encoding="UTF- 8 "?>
<web-app>
...
<security-constraint>
<web-resource-collection>
<web-resource-name>Scriptlauncherpage</web-resource-name>
<url-pattern>/*</url-pattern>
</web-resource-collection>
<auth-constraint>
<role-name>admin</role-name>
<role-name>scriptlauncher</role-name>
</auth-constraint>
</security-constraint>
<security-role>
<role-name>scriptlauncher</role-name>
</security-role>
<security-role>
<role-name>admin</role-name>
</security-role>
<login-config>
<auth-method>BASIC</auth-method>
</login-config>
</web-app>
WebApp /webswing-server¶
Webswing-server distinguishes between the admin page (role admin) and the script launcher (role scriptlauncher). The file <tomcat>/webapps/webswing-server/WEB-INF/web.xml must be extended as follows:
<?xml version="1.0" encoding="UTF- 8 "?>
<web-app>
...
<security-constraint>
<web-resource-collection>
<web-resource-name>Scriptlauncher</web-resource-name>
<url-pattern>/scriptlauncher/*</url-pattern>
</web-resource-collection>
<auth-constraint>
<role-name>admin</role-name>
<role-name>scriptlauncher</role-name>
</auth-constraint>
</security-constraint>
<security-role>
<role-name>scriptlauncher</role-name>
</security-role>
<security-role>
<role-name>admin</role-name>
</security-role>
<login-config>
<auth-method>BASIC</auth-method>
</login-config>
</web-app>
webswing.config¶
For the WebSwing admin page, embedded authentication must be retained; authentication by Tomcat does not take place. The users and passwords are specified directly in the “/” area:
"security" : {
"module" : "EMBEDED",
"config" : {
"users" : [ {
"username" : "admin",
"password" : "$hashed$oCxLZf6K1v57ujzfHBV461B2HunQJPtx6MCqYsftvlE"
"roles" : [ "admin" ]
} ],
"extensions" : [ ]
},
"classPath" : [ ],
"authorizationConfig" : {
"users" : [ ],
"roles" : [ ]
}
}
To encrypt passwords in plain text, the configuration must be saved (Apply) on the admin page.
The Tomcat user is transferred with the DcsTomcatSecurityModule to call the scripts. Configuration takes place in the /scriptlauncher area:
“security” : {
“module” : “DcsTomcatSecurityModule”,
“classPath” : [ “<tomcat>/webapps/sl/dcslib/dcsTomcatModule.jar” ],
“authorizationConfig” : {
“users” : [ ],
“roles” : [ ]
},
“config” : { }
}
To log in with a different user, Tomcat must be restarted.